- info@satcominfotech.com
- +91 22 49621040/41
Arcon

Privileged Access Management (PAM):
Privileged access
management (PAM) is an identity security solution that helps protect
organizations against cyberthreats by monitoring, detecting, and preventing
unauthorized privileged access to critical resources.
User Behaviour Analytics (UBA):
UBA is a cybersecurity
process regarding the detection of insider threats, targeted attacks, and
financial fraud that tracks a system's users. UBA looks at patterns of human
behaviour, and then analyses observations to detect anomalies that may indicate
potential threats.
Endpoint Privilege Management:
Endpoint Privilege
Management solution (EPM) grants endpoint privileges ‘just-in-time’ or
‘on-demand’ and monitors all end users for you. The tool detects insider
threats, compromised identities, and other malicious attempts to breach
endpoints. It has a powerful User behaviour Analytics component that takes note
of the normal conduct of end users and identifies atypical behaviour profiles
and other entities in the network.
Global Remote Access (GRA) :
GR is a remote desktop tool
that allows administrators to establish a remote connection within an enterprise
network to any client machine. In case of a problem, client users can allow
admins or help desk engineers to troubleshoot the machine in a controlled
environment.
Security Compliance Management (SCM):
SCM solution helps to
enforce a comprehensive IT risk management framework – a unified engine of all
IT risk management controls required to be implemented at different layers for
effective risk mitigation. The solution ensures the creation of a robust
security posture and ensures compliance.
Identity and Access Management (IDAM):
IDAM is a solution
that ensures the details of an employee’s overall employment tenure are
maintained and managed from a single console. This allows administrators to
perform access certification and review activity in a much faster and more
efficient manner. At the same time, the end users do not have to wait too long
to gain legitimate access to business applications, legacy applications, or IT
Infrastructure devices.
Single Sign-On (SSO):
SSO is an access management
capability decider that enables employees to access multiple disparate systems
by authenticating just once.
Surveillance Access Management(SCM):
Like with other IoT
systems, there are inherent security concerns that can lead to serious breaches
and hostile assaults. IP-based systems have varied topologies and technologies,
making them significantly more complicated and resulting in a much broader
attack surface. Robust surveillance access management is essential to thwart
insider threats, third-party risks, and advanced cyber-attacks. Surveillance
Access Management helps to ensure that any unauthorized access to target IP
Cameras is denied.
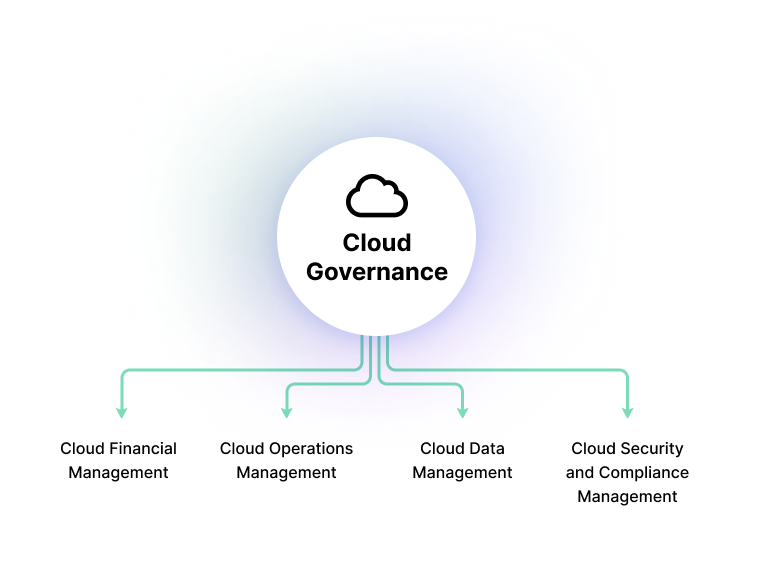
Cloud Governance :
Cloud Governance module can assist in
gaining total insight and control over your cloud infrastructure and workload.
It offers visibility into unnecessary rights, modifies regulations without
affecting developer processes, detects potential abnormalities, and enforces
access regulations across all users.
Enterprise Vault :
Enterprise Vault is a password
automation solution that helps eliminate risks arising from manual password
changes to critical service accounts, backed by a secure tunnel architecture and
proprietary encryption algorithm.
Related Products & Solutions
Satcom Infotech © 2024 / ALL RIGHTS RESERVED




.jpg)
.jpg)